What Is SSL Pinning and How It Works
Updated: October 18, 2025

SSL pinning is a security method that acts like a secret handshake between your mobile app and its server. Instead of just trusting any valid ID (a standard SSL certificate), the app is coded to accept only a specific, pre-approved certificate. This stops it from talking to impostor servers.
Understanding SSL Pinning Without the Jargon#

Think of a standard secure connection as a bouncer at a club checking for any valid government-issued ID. As long as the ID looks real and isn't expired, they let you in. This is how normal SSL/TLS works—your app checks if a server's certificate was issued by a trusted Certificate Authority (CA). It trusts the CA, so it trusts the certificate.
SSL pinning takes this a step further. Now, the bouncer has a very specific VIP list with your photo on it. Even if you show up with a perfectly valid ID, you're not getting in if your face doesn't match the photo on that list.
This "list" is a copy of the server's certificate (or just its public key) that gets embedded directly inside your mobile app. This simple technique forces the app to only accept a specific SSL/TLS certificate, rejecting any that don't perfectly match what's been "pinned."
Because the app flat-out rejects any certificate that doesn't match, SSL pinning dramatically increases security. It’s a powerful defense against sophisticated attacks, especially man-in-the-middle attacks where an attacker tries to use a fake or forged certificate. For a full rundown of defensive strategies, take a look at our guide on mobile app security best practices.
Standard SSL vs SSL Pinned Connection#
To really see the difference, let’s put a standard connection side-by-side with one that uses SSL pinning. The table below breaks down how that extra check adds a critical layer of security.
| Feature | Standard SSL/TLS Connection | SSL Pinned Connection |
|---|---|---|
| Trust Basis | Trusts any certificate from a known Certificate Authority (CA). | Trusts only the specific certificate or public key embedded in the app. |
| Verification | Checks if the server's certificate is valid and issued by a trusted CA. | Checks if the server's certificate is the exact one it expects. |
| Vulnerability | Susceptible to attacks if a CA is compromised or a fraudulent certificate is issued. | Highly resistant to compromised CAs and fraudulent certificates. |
As you can see, pinning moves the trust from an outside party (the CA) to the app itself, giving you direct control over who your app talks to. It's a fundamental shift that makes your app's communication far more secure.
How the SSL Pinning Process Actually Works#
To really get what SSL pinning is doing, let's first quickly walk through a normal secure connection.
Usually, when your app wants to talk to a server, it kicks off something called an SSL/TLS handshake. The server shows its ID card—its SSL certificate—and your app checks it. Your phone's operating system has a built-in list of trusted ID checkers, known as Certificate Authorities (CAs). If one of those trusted CAs has signed the server's certificate, the connection is approved.
SSL pinning basically adds a bouncer at the door. It doesn't just take the CA system's word for it. Instead, the app holds its own pre-saved copy of the server's legitimate certificate or public key. Think of it as having a photo of the only person it’s allowed to talk to.
So, during that handshake, right after the server presents its certificate, your app does its own private security check. It compares the certificate it just received from the server against the one it has "pinned" inside its own code.
The Decisive Checkpoint#
This is the moment of truth. The app is essentially asking, "Is this the exact certificate or public key I was told to expect?" If it's a perfect match, the handshake completes, and data starts flowing securely.
But if there's any mismatch at all—even if the certificate is technically valid and signed by a legitimate CA—the app slams the door shut and terminates the connection. No exceptions. This hard stop is what makes SSL pinning so powerful. It acts as an uncompromising gatekeeper, preventing any communication with a server that isn't the pre-approved one, effectively shutting down impostors.
By shifting the trust from a long list of external CAs to a single, developer-defined credential, SSL pinning gives the application direct control over its own security perimeter.
This infographic breaks down the workflow, showing how that simple pin verification step becomes the critical decision point.
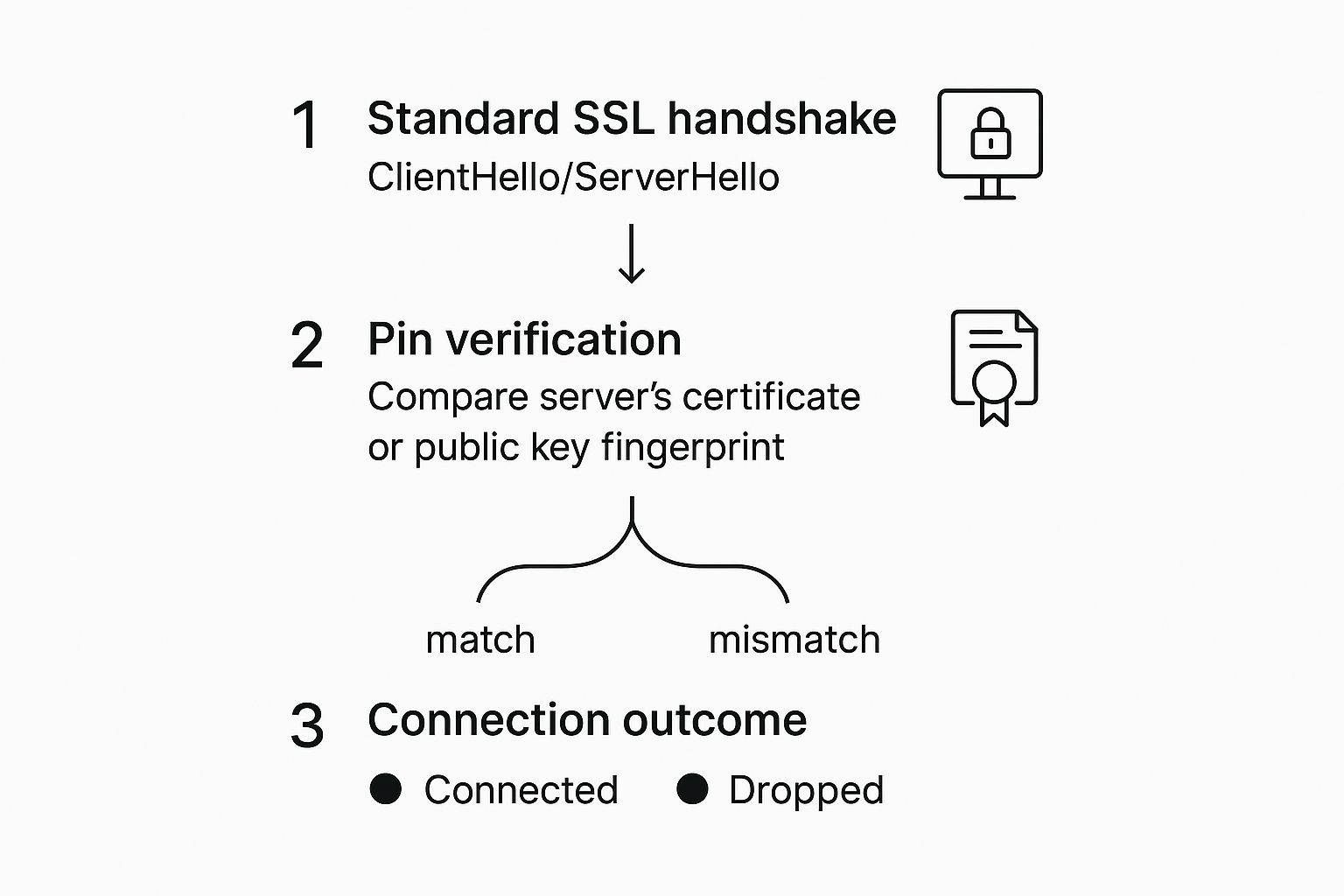
As you can see, the pin verification is a decisive fork in the road. It’s a simple concept, but it makes the entire connection process far more resilient against certificate-based attacks.
Why You Need to Guard Against MITM Attacks#

The number one reason we need SSL pinning is to shut down a nasty threat called the Man-in-the-Middle (MITM) attack. It’s a classic security nightmare, and it happens more often than you’d think.
Picture this: you’re grabbing a coffee and connect to what looks like the shop's public Wi-Fi. But it's actually a rogue network set up by an attacker. When your app tries to connect to its server, the attacker intercepts that request. They then present your app with their own fake—but technically valid—SSL certificate.
Without SSL pinning, your app is trained to trust any certificate signed by a recognized Certificate Authority. So, it accepts the fake one and opens a secure-looking connection. From that point on, every piece of data—passwords, credit card details, private messages—is funneled directly through the attacker's server. They see everything.
The Uncompromising Security Checkpoint#
This is exactly where SSL pinning flips the script. By "pinning" the server's real certificate or public key inside the app itself, you’re basically giving your app a VIP guest list. It knows who it's supposed to talk to and will refuse to connect with anyone else.
Now, when that attacker in the coffee shop presents their fake certificate, your app immediately spots the impostor. It doesn't match the pinned certificate on its list, so the connection is instantly terminated. No data is sent. The attack fails before it even begins.
By hard-coding the expected identity of the server, SSL pinning transforms your app from a trusting participant into a strict verifier, making it virtually impossible for MITM attacks to succeed.
This is a critical layer of defense. In fact, a survey of mobile security incidents found that apps without this protection had up to a 70% higher risk of data breaches from this exact kind of interception.
Protecting these communication channels is especially vital when building secure APIs that handle sensitive information, as those endpoints are prime targets. It’s also a key part of the puzzle when you're securing API keys to ensure they aren't captured in transit.
Choosing Between Certificate and Public Key Pinning#
When you decide to implement SSL pinning, you’ll hit a fork in the road. You can either pin the entire certificate or just the public key inside it. Each path comes with its own trade-offs, and your choice really boils down to how you want to balance tight security against day-to-day operational sanity.
Pinning the entire SSL certificate is the most straightforward approach. You essentially take a snapshot of the server's exact certificate and bake it into your app. This creates an incredibly rigid, one-to-one match, giving you absolute certainty that you're talking to the server you expect.
But that rigidity is also its greatest weakness. The moment that certificate expires and you renew it—even if you use the exact same key pair—the new certificate is a technically different file. Your app, loyal to the old certificate, will immediately reject the new one. This breaks connectivity for every single user until they update their app.
The Flexibility of Public Key Pinning#
This is why most developers opt for public key pinning. It’s a far more flexible and resilient method. Instead of locking your app to the entire certificate file, you only pin the public key contained within it.
The real magic here is that you can renew your SSL certificate as often as you need to. As long as you generate the new certificate from the same key pair, the public key doesn't change. Your app will happily trust the new certificate without ever needing an update.
This approach gives you a rock-solid security guarantee while dodging a massive maintenance headache down the line. It fits perfectly with modern infrastructure, especially when you're building robust communication channels like those we cover in our guide to RESTful API design principles.
To make it crystal clear, let's put these two methods side-by-side.
Certificate Pinning vs Public Key Pinning#
This table breaks down the key differences to help you decide which approach makes sense for your project.
| Aspect | Certificate Pinning | Public Key Pinning |
|---|---|---|
| Flexibility | Low. The app breaks on any certificate change, including routine renewals. | High. Lets you renew certificates freely as long as the key pair stays the same. |
| Maintenance | High. Forces a mandatory app update for every single certificate renewal. | Low. Drastically cuts down the need for frequent, forced app updates. |
| Best For | Niche situations with extremely long-lived, static certificates (which is pretty rare). | The vast majority of mobile apps, offering the best balance of security and practical management. |
For almost every real-world scenario, public key pinning hits the sweet spot. It locks down your app’s connections without turning every certificate renewal into a full-blown crisis.
Navigating the Challenges of SSL Pinning#

While it's a huge security win, SSL pinning is absolutely not a "set it and forget it" solution. It introduces a massive operational headache that, if you mess it up, can be catastrophic for your app: certificate rotation. This is the single biggest challenge you'll face.
Here’s how it can go wrong. Imagine you've pinned a specific server certificate inside your mobile app. That certificate, like all of them, has an expiration date. When it expires, you issue a new one to keep your server secure. Simple enough, right?
The problem is your app—still holding onto the old, expired pin—suddenly sees the brand-new, perfectly valid certificate as an impostor.
The result is a total communication breakdown. Your app will flat-out refuse to connect to your server. For every single user. This effectively "bricks" your application, making it completely useless until people download an updated version with the new certificate pinned inside.
Avoiding Accidental Service Outages#
This exact scenario is why careful planning is non-negotiable. The history of web security is littered with cautionary tales. For example, HTTP Public Key Pinning (HPKP) was a similar standard for browsers that was eventually deprecated because the risk of accidentally creating widespread outages was just too high. You can read the OWASP community's analysis for the full post-mortem.
To avoid the same fate, you have to build resilience directly into your pinning strategy from day one. Here are a few best practices:
- Pin Backup Keys: Never, ever rely on a single pin. Pin the public key of your current certificate and a backup key. When it's time to renew, you can issue the new certificate using that backup key, which gives you a seamless transition without forcing an immediate app update.
- Implement a Dynamic Approach: Some more advanced strategies involve fetching updated pins from a secure, secondary source. This definitely adds complexity, but it can give you a way to update pins without having to push a full app deployment through the app stores.
- Monitor Expiration Dates: Treat certificate expiration dates like critical deadlines. Set up automated alerts way in advance to give your team plenty of time to manage the rotation process without any last-minute panic.
These operational details are crucial, especially when you're integrating complex features like an in-app web browser that might need to connect to multiple domains with different security policies.
Common SSL Pinning Questions Answered#
Let's clear up a few of the questions that always pop up when teams start talking about SSL pinning. Getting a handle on its role, its limits, and what it means in the real world is the key to using it right.
Is SSL Pinning Necessary for All Apps?#
Honestly, not every single app needs it. But if your application handles anything sensitive, it's a must-have. We're talking about logins, payment details, personal health records, or private messages. For any banking, healthcare, or e-commerce app, it's not just a good idea—it's an essential layer of security.
If your app just shows static, public content, then the extra work to set it up and maintain it might not be worth it. For most modern apps, though, the protection it offers against common attacks is a smart investment. It shuts down an entire category of security holes with one solid implementation.
Does SSL Pinning Replace Standard SSL/TLS?#
Not at all. Think of it as an enhancement, not a replacement. SSL pinning works right on top of the standard SSL/TLS protocol you already use. Your server still needs a valid certificate from a trusted authority, and the normal SSL handshake still happens just like before.
Here’s a good way to think about it: SSL/TLS confirms the server has a valid ID, like a driver's license. Pinning is like your app checking that license and saying, "Okay, not only is this a valid ID, but it's the exact one I was told to expect." It doesn't replace any part of the security chain; it just makes it much stronger.
SSL pinning doesn't eliminate the need for traditional certificate validation; it adds a crucial, client-enforced layer of specificity to it, ensuring your app only talks to the server it knows and trusts.
This extra check is what makes it so powerful. It’s especially critical in frameworks where you're building for multiple platforms from one codebase. For example, when you build a Capacitor mobile app, pinning can lock down the shared API connections that your iOS and Android apps both rely on.
What Happens If a Pinned Certificate Expires?#
This is the big one—the single greatest risk of a poorly managed pinning strategy. If the certificate you pinned on the server expires and you swap it out, your app will immediately reject the new, perfectly valid certificate. Why? Because it no longer matches the one "pinned" in its code.
This instantly breaks the connection to your server, making the app completely unusable for all of your users. They won't be able to connect again until they go to the app store and download an updated version with the new certificate info pinned inside. That's exactly why having a rock-solid plan for certificate rotation and backup keys isn't just a suggestion—it's absolutely crucial.
Ready to build secure, native mobile apps without the native-development headaches? The NextNative toolkit gives you everything you need to go from Next.js to iOS and Android, fast. Check out the toolkit at https://nextnative.dev.